We've been developing an event-driven architecture to power use cases in security observability. Using our behavioural analysis backbone, this system collects security events throughout the SDLC from various collectors, groups them based on baseline intelligence and user guidance (such as whitelists), and surfaces alerts in case of anomalies.
Events are served through a highly configurable webhook API, allowing for action triggers and import into custom sinks (such as SIEM)
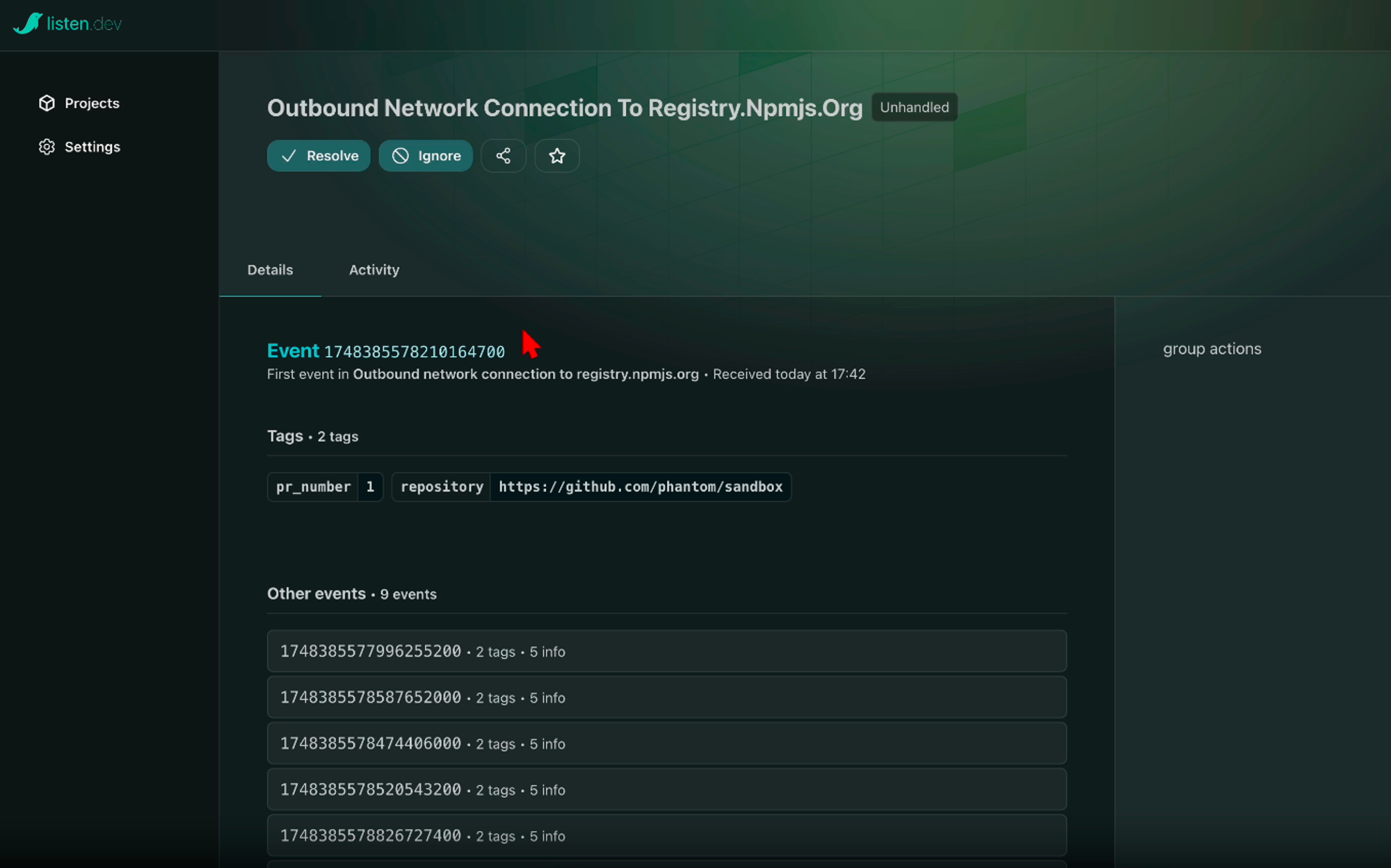
A sneak peek into our new interface:
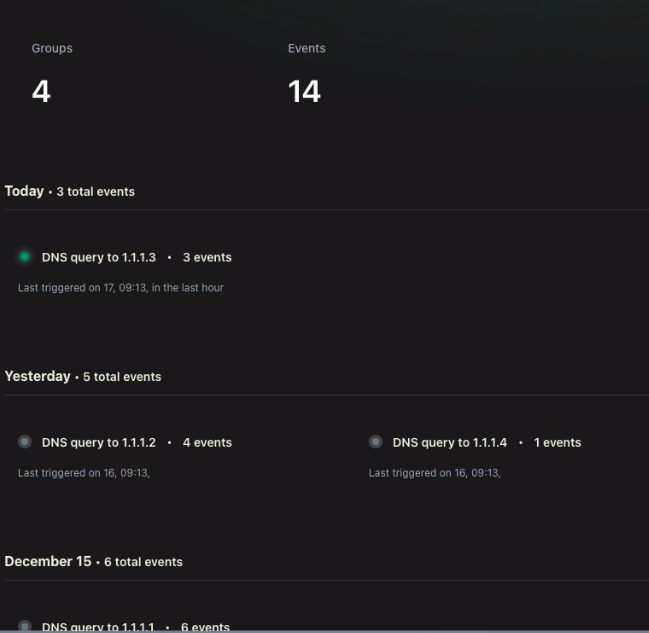
Use case example
The npm package puppeteer interacts with Chromium in its regular state. At every build, our sensor captures this behavior and groups similar events to establish a baseline. In case we observe a change (such as a new transitive dependency introducing a suspicious network source), an alert is triggered through a webhook with relevant context around the event—including tags representing owner, execution trace diff, service of origin, and other details gathered from our collection. We intend this to be highly configurable, including the ability to import the JSON into your own SIEM.